In the era of digital transformation, the business process landscape is not the only aspect undergoing significant changes; the darker side of life is also experiencing a digital metamorphosis. The vast digital interconnectivity driving global business processes has become a promising target for cybercriminals. Cybersecurity incidents affecting organizations and companies are often caused by vulnerabilities in their IT infrastructure and systems.
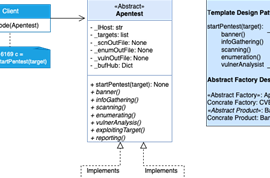
To address these vulnerabilities, organizations must continually update and evaluate their security posture. Strengthening this posture is only possible when vulnerabilities in the system are identified. The process of discovering these security vulnerabilities can be achieved through a security testing method known as penetration testing (Pentesting) or ethical hacking. However, the challenge lies in the fact that the pentesting process is time-consuming and involves several stages, including information gathering, network scanning, enumeration, vulnerability research, exploitation, and reporting. This complexity often requires the involvement of cybersecurity experts.